DeRF Documentation Home
The DeRF, an open-source tool available on GitHub, consists of Terraform modules and a Cloud Run application written in Python. Within this package, a variety of built-in attack techniques are provided, focusing on targeting AWS and GCP. For a complete accounting of all built-in attack techniques, refer to the list in documentation.
The DeRF deploys and manages the target cloud infrastructure, which is manipulated to simulate attacker techniques. Terraform is used to manage all resources, deploying (and destroying) hosted attack techniques and target infrastructure in under 3 minutes.
While a bring-your-own-Infrastructure (BYOI) model isn't currently supported, maintaining The DeRF infrastructure costs less than $10/month for Google Cloud and $5/month for AWS. The tool's convenient deployment model means you can use it as needed rather than continuously running 24/7. Check out the deployment guide for more details.
Key features of this tool include:
• User-Friendly Interface: Since the DeRF is hosted in Google Cloud, End Users can invoke attacks through the cloud console UI without the need to install software or use the CLI.
• Accessibility for Non-Security Professionals: The DeRF caters to a broad audience of End Users, including Engineering, Sales, Support Staff, or automated processes.
• Robust OpSec: Long-Lived Credentials are not passed between operators, instead access to the DeRF and its attack techniques are controlled through GCP IAM Role-Based Access Control (RBAC)
• Extensibility at its Core: Attack sequences are written in YAML, enabling easy configuration of new techniques.
• Turn-Key deployment: Deploying (and destroying!) the DeRF is a fully automated process, completed in under 3 minutes.
High Level Architecture
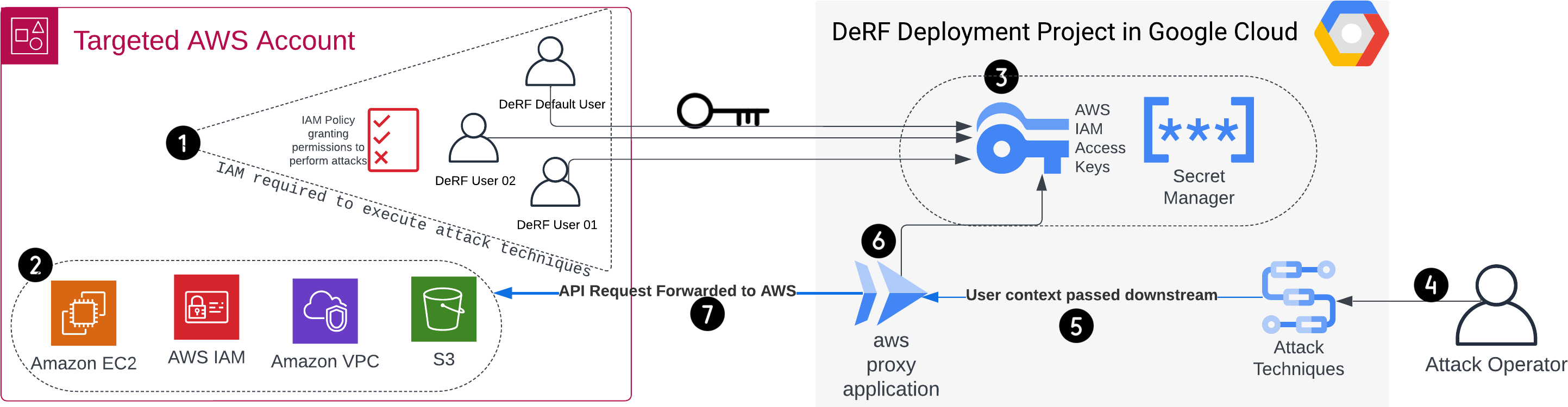
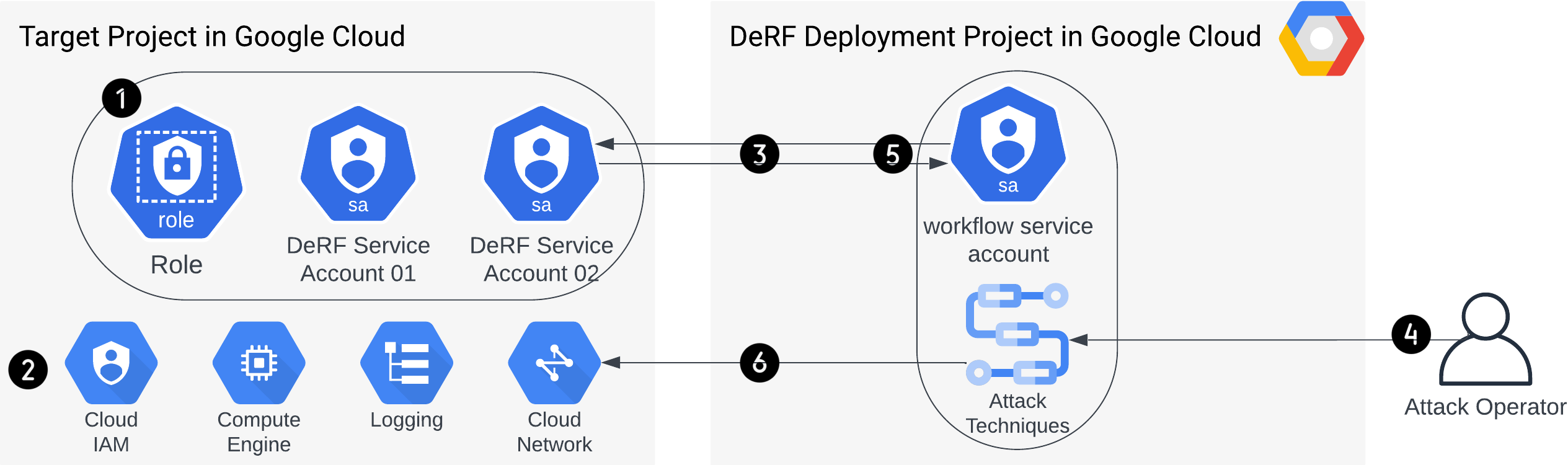
The DeRF’s unique architecture is wholly deployed via terraform. It consists of resources spread across AWS and GCP.
DeRF Attack Architecture for AWS
DeRF Attack Architecture for GCP
DeRF User Personas
See the User Guide for more detailed descriptions of the permissions assigned to the DeRF Execution and Default Users.
The DeRF Deployment User deploys the DeRF terraform module across AWS and GCP. Permissions required for the DeRF Deployment User are documented here
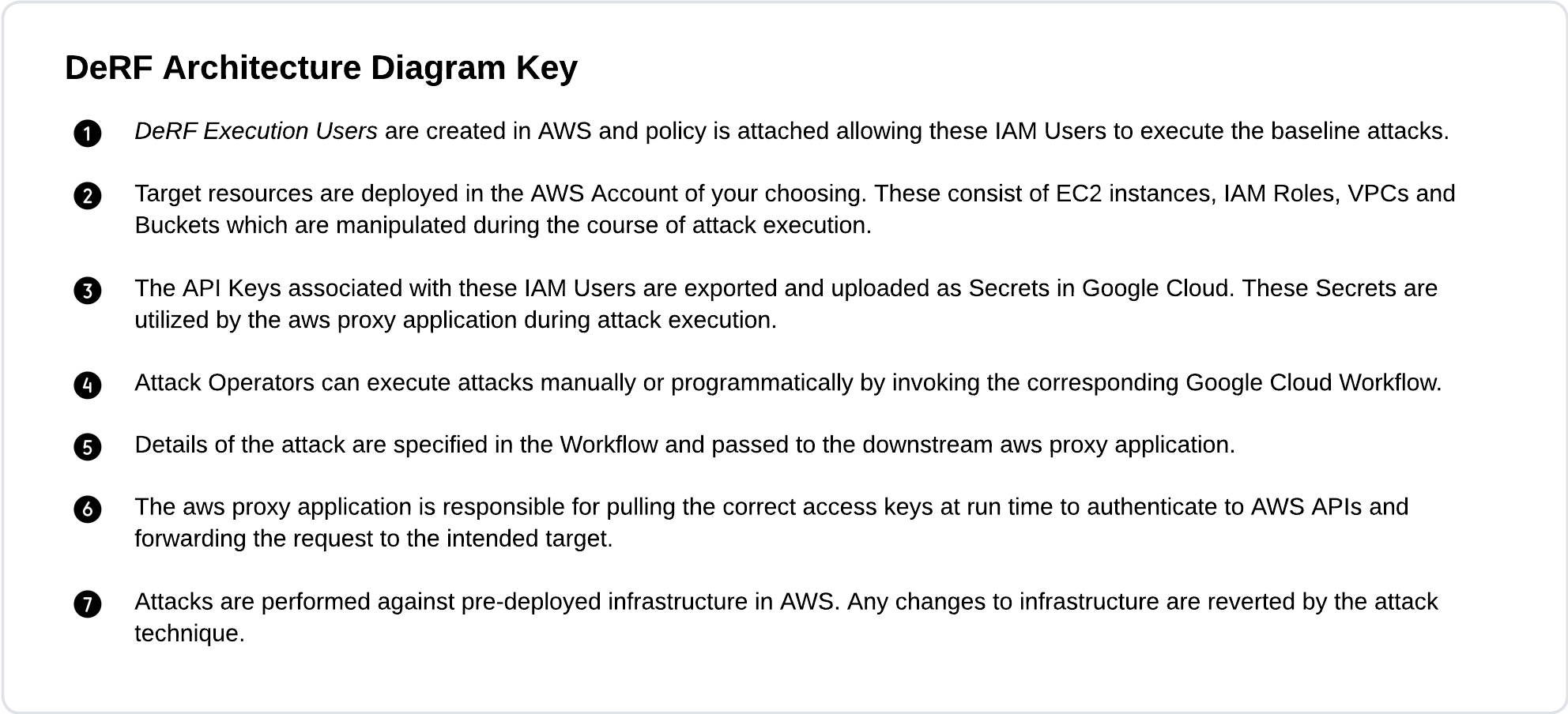
The DeRF Execution User 01 is one of two built in an AWS IAM Users which AS attack techniques can run as. Permissions are assigned to the derf-execution-users AWS IAM Group and documented within each attack module.
The DeRF Execution User 02 is one of two built in an AWS IAM Users which AWS attack techniques can run as. Permissions are assigned to the derf-execution-users AWS IAM Group and documented within each attack module.
The DeRF Default User is an AWS IAM User used by attack techniques to revert state changing actions by the AWS attack modules. If AWS attack techniques are run with the user parameter left blank, the attack with default to run as this user.
In order to perform an attack as an arbitrary AWS Role, AWS IAM Temporary Session Credentials generated from IAM Roles can be passed directly to the aws-proxy-app as Post Body Parameters additionally with the TEMPCREDSPASSED = yes Post Body parameter.
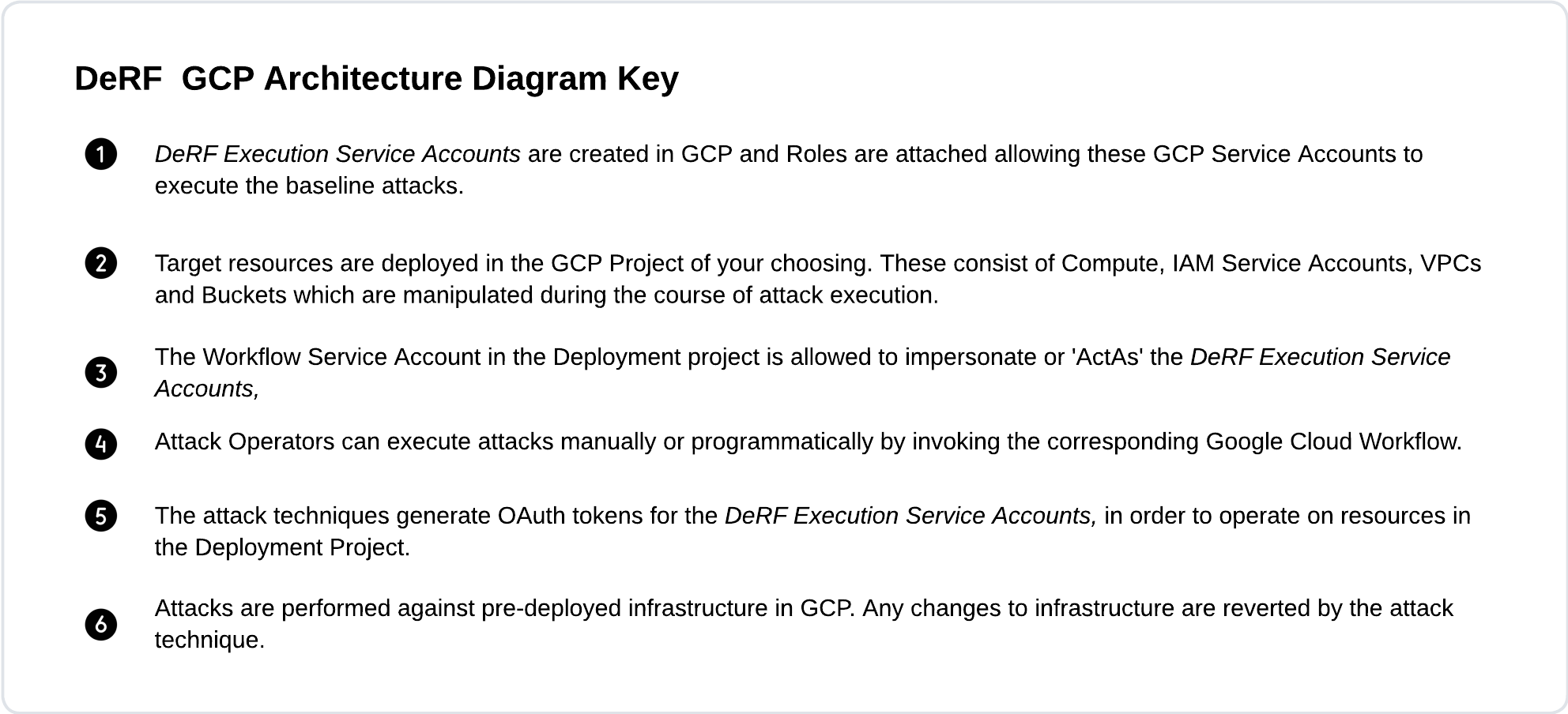
The DeRF Service Account 01 is one of two built in Service Accounts which GCP attack techniques can run as. Roles are assigned to these two DeRF Execution Service accounts in the targeted Project as part of tool deployment.
The DeRF Service Account 02 is one of two built in Service Accounts which GCP attack techniques can run as.Roles are assigned to these two DeRF Execution Service accounts in the targeted Project as part of tool deployment.
Video Demo's
Watch this tutorial to understand, what is the DeRF, how to use it and how deploy in your environment.