EC2 Shared EBS Snapshot
Platform: AWS
MITRE ATT&CK Tactics
- Exfiltration
Description
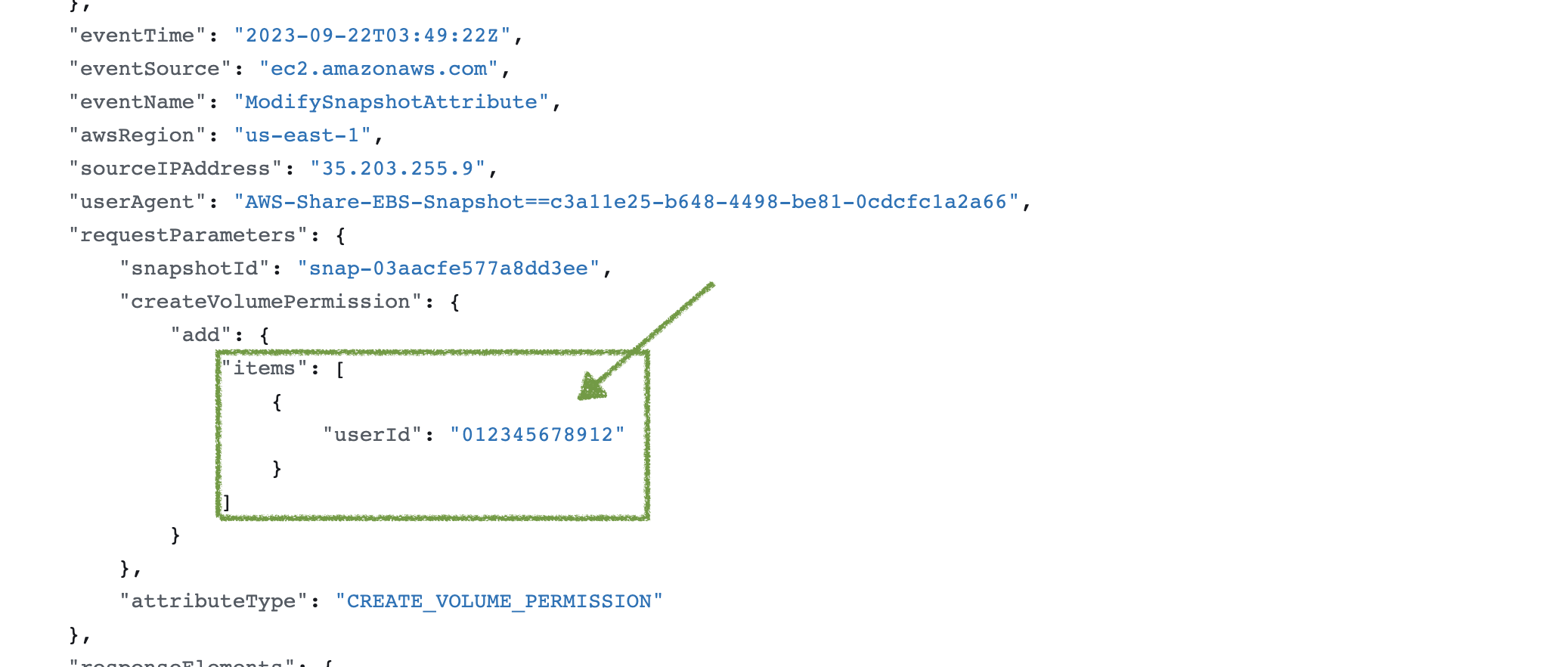
This attack shares an EBS Snapshot with an external, fictitious AWS account, (012345678912)
Attacker Actions:
- Updated the attributes of an EBS Snapshot to an external, fictitious AWS account.
- Resulting event name:
ModifySnapshotAttribute - Assigned IAM Permission:
ec2:ModifySnapshotAttribute
Workflow Inputs:
Specify which user this attack should run as.
Clean Up:
- Removes the fictitious external AWS account by calling the
ModifySnapshotAttributeAPI again, this time removing the permission. - Executed as the
DeRF Default User
Execution Instructions
- See User Guide for Execution Instructions via the Google Cloud Console
- Programmatically execute this workflow with the following cli command:
Detection Artifacts
Identify when an EBS Snapshot permission is modified with the ModifySnapshotAttribute event, specifically when the requestParameters.createVolumePermission contains an "add" object" and the key add.items[].userId is an external AWS Account.
Refer to Stratus Red Team documentation for additional detailed detection artifacts produced by this attack technique.